Definition
Kerberoasting is a very popular attack and is a quick way to get domain admin in a network, Kerberos takes advantage of services account (each service account has a Service Principle Number).
Service accounts are user accounts that are created explicitly to provide a security context for services that are running Windows Server operating system, usually service accounts are in the “Domain Admins (DA)” group. Which can dump the hashes of a DC!.
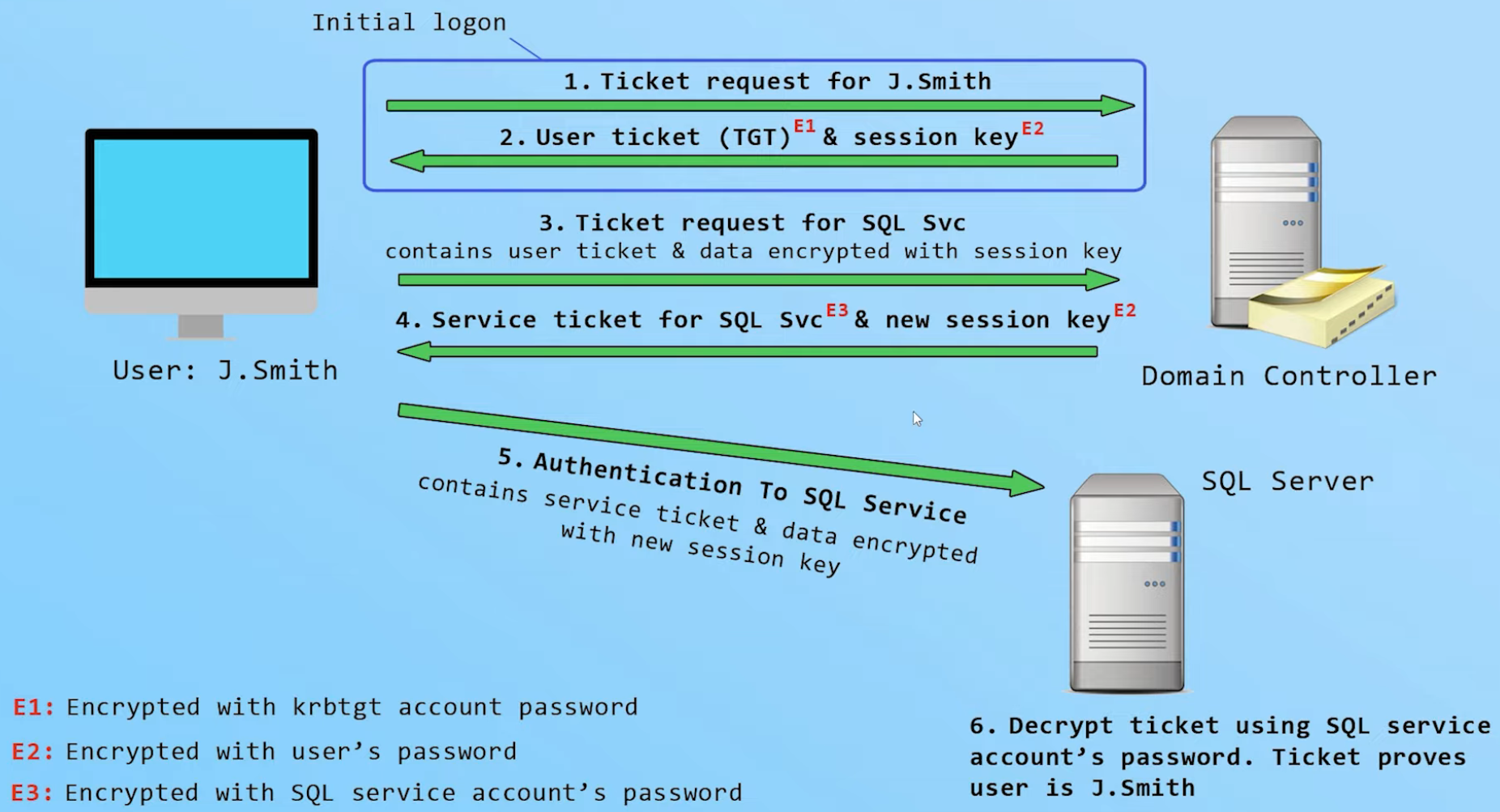
Legitimate Kerberos process:
- Request a TGT, provide username and password to the KDC (DC in this case)
- Receive a TGT from the KDC (ANYONE CAN ASK AND RECEIVE IT!)
- Request a service ticket (TGS) from the KDC, but we need to provide our TGT
- KDC sends back the TGS to us WHICH IS ENCRYPTED WITH THE SERVER’S OF SERVICE ACCOUNT HASH
- The server will decrypt that hash to see if we have the right to access this service or not
Executing Kerberoasting
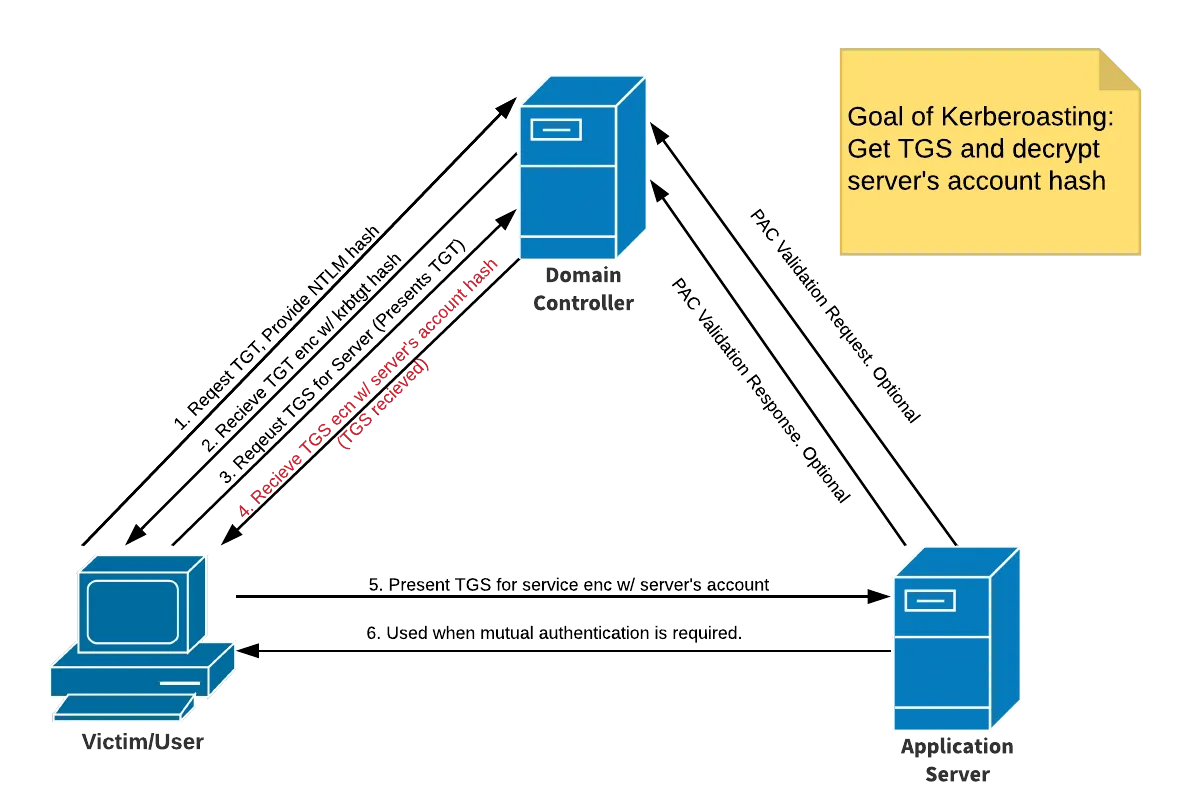
As we have seen in the process above, anyone can request TGT which can be used to get the TGS which is encrypted with the server’s of service account hash. The idea behind this attack is to get SPNs available in the domain and crack their hashes to gain service account:
- Get SPNs available and dump hashes
sudo GetUsersSPNs.py <domain-name>.local/<username>:<password> -dc-ip <dc-ip> -request- Crack hashes using hashcat
hashcat -m 13100 kerberos.txt /usr/share/wordlists/rockyou.txtKerberoasting mitigation
- Strong password
- Least privilege (service accounts don’t have to be domain admins!)